A bunch of articles have been written about a new virus that is supposedly sweeping through Apple’s (NASDAQ:AAPL) Mac OS X operating system. A quick investigation demonstrates that most of these articles are less than accurate. S|A will walk you though the path we took, so you can see what we found. UPDATE at bottom.
Exactly when the excitement started is hard to be certain. One of the earliest articles we managed to find was published on May 2, 2011, and was titled: Coming soon to a Mac near you: serious malware. Quoted from the article:
The first advanced DIY (Do-It-Yourself) crimeware kit aimed at the Mac OS X platform has just been announced on a few closed underground forums. … The kit is being sold under the name Weyland-Yutani BOT and it is the first of its kind to hit the Mac OS platform. Apparently, a dedicated Ipad and Linux release are under preparation as well.
Note the highlighted words above. Weyland-Yutani is of course a reference to the profit before ethics mega-corporation in the Alien movies.
Think about the Ipad version. Because of the way that the Ipad/IPhone/IPod Touch software system works, the only way that a Weyland-Yutani BOT produced piece of malware could get widely installed, would be if it was approved for sale through the Apple App Store. Apple is very careful about what software is approved for the App Store to weed out rogue applications like this. The industry press knows this. Why is it printing this nonsense? Yes, you can jailbreak your Ipad, and a small percentage of Ipad owners will do so, and use an alternate app store like Cydia. But the people running the Cydia App Store are as careful as Apple – report a rogue application to them and it will be removed.
The Linux version is problematic. S|A is going to assume that they actually mean Android, since it’s the version of Linux with the greatest market share. But an Android version of this kit would have the same problems that an Apple version has. Google doesn’t vet applications as carefully as Apple does, this is true, but Google does vet them. Google also nukes rogue applications, and warns people who have installed the rogue application. In other words, it’s a useless attack vector that isn’t going to make the attacker any money.
The OS X version is nothing new. This could have been done any time since Mac OS had TCP/IP support built directly into the operating system. In fact it’s just a minor variation on a remote control system. There’s nothing noteworthy about it. Similar systems have been used in online gaming for years, where one player has been able to control other players who were ‘away from keyboard’ using a scripting engine (this was a common way of playing Trade Wars 2002)
Anyone else could have produced something along the same line years ago. It’s dirt simple. It’s just if more sinister types were doing it, they wouldn’t have announced it. They would have just done it, and then built it into a library that was useful, and given the library away for free. Anyone could have built in random call home routines, so that any program the library was incorporated into would call home once every month or so, and if it didn’t manage to connect, it would wait another month before trying again.
The Malware
The articles we have seen called the attack vector a Computer Virus. A Virus is program that is capable of penetrating the target system and self replicating without operator intervention. The attack vector described however is actually a Trojan. This is an important distinction. A Trojan cannot penetrate the target system without operator intervention. The operator has to be tricked into allowing the Trojan into the system through a Social Engineering style attack. If the operator cannot be tricked, the Trojan cannot penetrate the system.
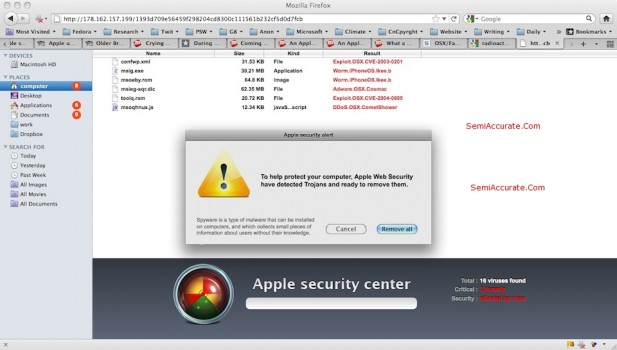
The attackers don’t advertise their attack sites, so to fully evaluate the attack S|A had to search for a site, and then fake the site into thinking it was infecting our computer. We used a MacBook Pro 13″, and went looking through Google Image Search, and soon enough we found a site. Below is a screen cap.
At this point all we can say is Think of it as Evolution in Action. Seriously. When this screen came up we spent most of the next fifteen minutes rolling around on the floor laughing.
To help protect your computer, Apple Web Security HAVE detected TROJANS and READY to remove them.
Yeah, right. We have a company which is famous for spending millions of dollars on getting the exact size and shape of the product packaging right, and it screws up on basic grammar? Pull the other one, it’s got bells on. This was obviously not something Apple produced that we were surprised anyone had fallen for it.
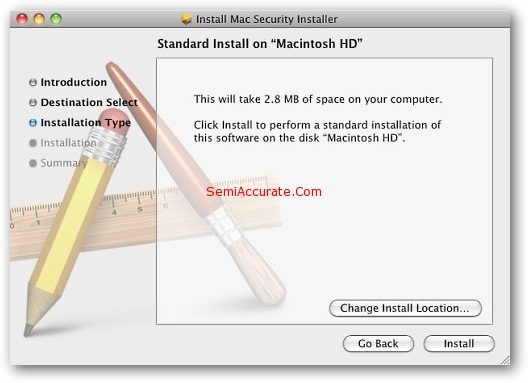
Apple is proud of their software. Very proud. As a company Apple goes to great lengths to brand each software product. The above installer uses a generic template, something that Apple would never, ever, do. For that matter Apple does not deliver software via website download any more. All software downloads come through Apple’s Mac OS X Application Store, and every Mac owner knows this. Apple has gone to great lengths to make sure that everyone knows it, minus those strange linux users who cannot access their app store. Needless to say we killed the install, since we didn’t want to give the jokers at the other end access to the S|A Corporate American Express Card. Not that they could do much damage to it anyway, we’ve got it maxed out at our five dollar limit already.
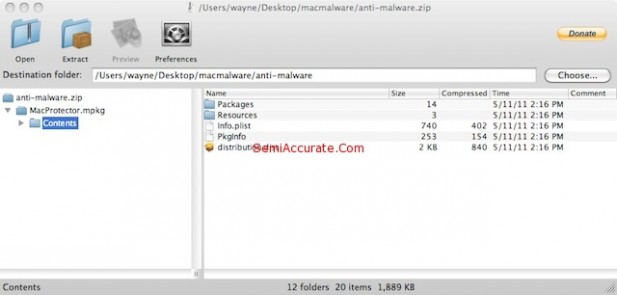
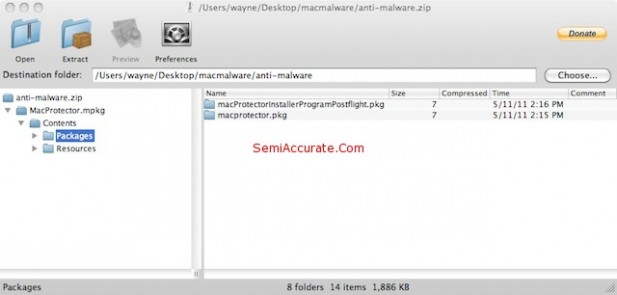
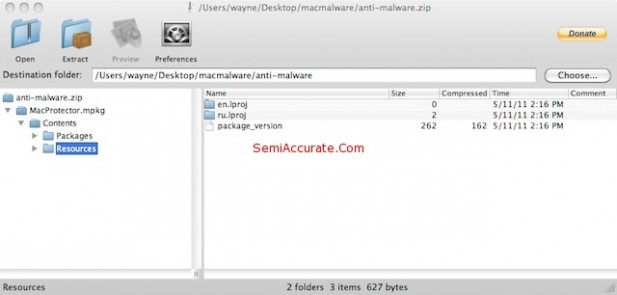
We do however have the entire download, and we spent sometime taking it apart.
We then called Apple, and had an interesting conversation with an Apple representative. Apple really didn’t want to talk to us. It took some some significant persuasion on our part to get them to open up as much as they did, which wasn’t very much.
Apple finally confirmed that there had been some cases where users had been taken in. They wouldn’t give numbers, but based on a check of the Apple forums, the numbers don’t seem to be all that high.
Apple staff also confirmed to S|A that document number EM406 is a valid Apple internal technical article number, and that the title is correct. Apple would not confirm if the copy that S|A has in our possession is Apple’s document EM406.
For those who have been infected, Apple is not recommending a specific action at the present time, because Apple is not certain that it has a solid solution. If Apple recommends a solution that does not totally remove the Trojan, it could do more damage, by giving the user a false sense of security.
What is This?
Technically as stated, this is a Trojan, named after the mythical Trojan Horse (and not the brand of condoms – though if you are really nice S|A might some day tell you about the time that a woman of great respect, and also our acquaintance ordered twelve gross of condoms for a hospitality suite…). A Trojan is a computer program which is disguised as another program. One famous example was Yankee Trader Registered V 5.00 (YTR500.ZIP or YTR500.ARJ) which pretended to be a popular game, but when ran, formatted all local drives, and every networked drive which the account used to execute the program had sufficient permission to access.
Trojans have always been possible on Mac OS X, or for that matter on Microsoft Windows. Consider Safari (or IE). What if someone at Apple (or Microsoft) had added code to capture all keystrokes from Safari (or IE) to a file, and then to filter out the generic garbage, so that it only kept the good stuff, things like credit card or banking information? And have the program then report that information to a website in the background so that the user isn’t aware of anything happening? That would be a classical Trojan, and is the sort of thing that Apple, Microsoft, Opera, and Mozilla worry about. Because it’s really not all that hard to add code to do something like this, so they have to watch their staff carefully to make sure that no one is suddenly driving a Ferrari on a janitor’s wages.
Unlike the Virus problems which the various versions of Microsoft Windows have suffered from for years, Apple Macintosh OS X has been virus free due to differences in the architecture of the operating system. While ‘arbitrary code execution’ attacks against OS X have been theoretically possible, and while Apple has patched against this sort of attack, to the best of our knowledge there has never been an attack seen in the wild.
Trojans are another thing. With a Trojan you have to use Social Engineering to convince the target to install the malware. With this specific attack, the target visits a web site, is shown a scare message, and a download starts. The entire attack fails if the target doesn’t install the software. And if the target reads the web page, they’ll know that it’s a fake. Bad grammar, misspelled words, and of course the knowledge that this is not how Apple normally delivers software.
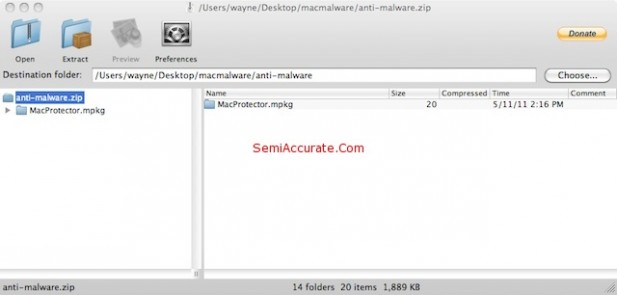
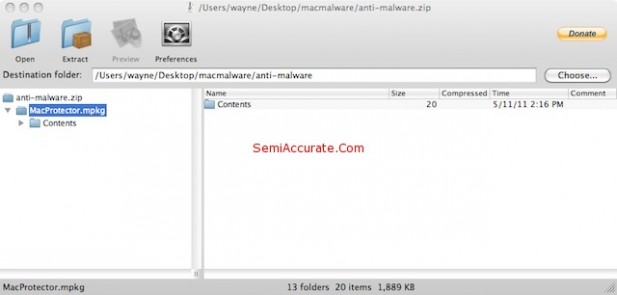
Deconstruction of a Trojan
With some glee we took the Trojan apart. It’s just a basic Mac OS X application. Here’s a series of screen caps showing the internals.
As we stated earlier – this is nothing other than a standard Mac OS X application. It’s a nasty Mac OS X application, but it’s nothing that could not have been written at any time since Cheetah was released in March of 2001. In fact it’s almost certain that something like this has been released at some time during the last ten years, people being people. And since there’s a lot more Windows users than Mac users, and a lot more Windows programmers than Mac programmers, there have almost certainly been far more Windows Trojans like this than Mac Trojans. And it appears that the Mac Trojans have had almost no effect.
So why all of the excitement?
That’s a good question. Consider the targets of Weyland-Yutani BOT. We have Apple Mac OS X, Apple IOS, and Linux (probably Android OS). And what is the one thing that the three operating systems have in common? All three have been taking market share from an operating system that Microsoft produces. Isn’t that curious. It does make one wonder.S|A
Updated Thursday, May 26th
As a follow up, Apple has now issued an official statement. It also reminds Apple users that
Note: Apple provides security updates for the Mac exclusively through Software Update and the Apple Support Downloads site. User should exercise caution any time they are asked to enter sensitive personal information online.
Wayne
Wayne Borean
Latest posts by Wayne Borean (see all)
- Darwin does Free Software - Jun 28, 2011
- The Nokia-Apple Patent Deal - Jun 28, 2011
- The Mac OS X Virus That Wasn’t - May 24, 2011
- Microsoft Death Watch* – Microsoft Buys Skype - May 11, 2011
- Patent Wars: Oracle v. Google Part 2 - May 9, 2011