Intel doesn’t understand security, but they are not shy about shouting it from the rooftops. They took a good idea, vPro, and turned it into a remote exploit and security risk that prevents a compromised machine from being repaired.
Intel doesn’t understand security, but they are not shy about shouting it from the rooftops. They took a good idea, vPro, and turned it into a remote exploit and security risk that prevents a compromised machine from being repaired.
You might recall, that vPro is the marketing name for a set of technologies that Intel fuses off on the majority of their CPUs, then sells it back to you at a higher price. They have managed to convince buyers that this is somehow a good thing, and the dumb sheep out there, that would be you, actually believe the iSomethingmeaningless marketing scheme adds value. To you that is, it definitely adds value to Intel stock.
The heart of this tech is a small and totally undocumented microcontroller/CPU in the chipset. If you don’t have an iSomethingmeaningless with a 5 or a 7 at the end, $50 more thank you, they helpfully turn it off for you. Maybe, it is inaccessible, but the vulnerabilities in it are likely still present, but Intel refuses to talk about that. No points if you can figure out why.
This controller was the heart of their failed antivirus-on-hardware Mk1, now labelled with McAfee branding in whatever revision this is. The first one was a bright idea on paper, put simple wire speed pattern matching in closed loop hardware on the chipset, so things coming in across network ports will be filtered before they can do any damage. Great idea, right?
On paper, yes. In reality, no one designing this whole complex technical scheme, EE PhD’s, managers, firmware developers, or the rest seemed to understand what the term false positive meant. No, I am not joking, whoops hardly seems like a fitting descriptor for this, but that is exactly what happened. Simple pattern matching with no ability to check for false positives on a high bandwidth data stream. Doh! Strangely, that concept faded away in short order, but the brilliant people who brought you that debacle seem to still be at Intel and working on more dangerous and less documented features.
The reason I am blathering about this is Intel’s “Small Business Advantage” software bundle that they are releasing today with the new and reassuringly more expensive vPro enabled Ivy Bridge chipsets. The phrase ‘Mistake of monumental proportions’ comes to mind, but somehow the company declined to name it “Intel Security Risk Technology with Remote Exploit Capabilities: Unavoidable User Lockout Technology”. The Remote Exploit would of course only be available in iSomethingmeaningless 7 CPUs for an extra $150 though, it took a lot of work to do something this stupid, and Intel has margins to meet.
Small Business Advantage (SBA) is a bundle of ‘technologies’ that mostly don’t actually work, and almost exclusively are things that could be done vastly better if you use non-Intel solutions. They are, in no particular order, Intel Identity Protection Technology, McAfee ePolicy Orchestrator Deep Command, Intel Secure Key, Intel OS Guard, Intel AMT 8.0, and Keyboard Video and Mouse module for Windows Powershell.
We covered some some of this debacle earlier here when they were released with Ivy Bridge CPUs. Lets suffice it to say that if you have an ounce of common sense, you will avoid paying extra for these ‘technologies’ like the plague. The new vPro based additions however need a bit of scrutiny, not because of why they are a good thing, but because of why you should avoid them. If you install these ‘technologies’ for ‘security’, you actually make securing your network impossible. No, it is worse than that, you actively give bad guys remote exploits, and once they are in, especially with Ultrabooks, there is literally no way to get them out.
As we said with the Ivy Bridge launch, the new technologies make it possible, almost easy actually, to have your system remotely but silently exploited. Like the non-logging monitoring port in Cisco hardware that lead to an unnamed foreign government walking all over Google’s IT resources, undetectably, for months, Intel is bringing this type of ‘advantage’ to ‘small businesses’. Yes, with SBA, you too can be undetectably exploited for months at a time, and pay extra for it. Are we finally seeing the new McAfee role?
I am not joking. The entire system is based on TXT, Intel’s undocumented chipset controller and crypto processor in every chipset they make. Since they are the only ones that can make chipsets for Intel CPUs now, if you buy Intel, you can’t avoid the holes. Intel will scream at anyone that dares suggest that the hardware security is flawed, but, well, it is. If you look here, this very very low profile footnote that was published last December, there are exploitable holes in TXT. Luckily for Intel, the undocumented nature of this debacle is keeping things secure. Security by obscurity is a great thing. If you are a hacker, if you are trying to secure something, it is about the worst vendor practice that you can face.
Luckily for us all, the brilliant hackers at Invisible Things Lab didn’t actually give up like all hackers automatically do when told that the TXT and related bits was undocumented. That was sarcasm for those who’s browsers do not support HTML 7.1 <Sarc_blink> tags. No, they just tore it to bits, then told Intel about it on December 10, 2008. Fair enough. Intel patched the vulnerability in a timely fashion, releasing a patch on December 5, 2011. Please note, the timely bit was sarcasm again, it took Intel *THREE* *YEARS* to patch an fundamental exploit in their hardware. (Editor’s note: Actually it was a few days short of 3 years exactly.)
The problem for Intel was that Invisible things, doing the correct and ethical thing, told Intel privately about the problem. Intel appears to have stonewalled them, not taken it seriously, and still wouldn’t document the TXT and related ‘security’ features. How do we know? Joanna Rutkowska gave a talk on it at Black Hat. In February of 2009. For the math averse, that would be more than 2 months after they told Intel, and after Intel completely stonewalled them. It then took Intel another *34* *months* to patch this little fundamental hardware vulnerability with two proven exploits. If you think we are kidding, check out Joanna’s blog here and read the presentation linked. To make matters worse, Intel continued to produce vulnerable hardware for literally years after they were made aware of this rather fundamental security vulnerability.
Why did we go off on this “TXT is badly insecure and overseen by chimps” tangent? Well, because the new Intel Small Business Advantage is all based on this known and proven insecure system. Official word from Intel was that it is provably secure and unbreachable, any everyone should just trust their word on it. It was then breached and proven insecure, but somehow, Intel’s official word did not change. Exploits were made. Intel swiftly responded within a timely 3 years, barely, that is more sarcasm. Now they are upselling you in the name of security while actually forcing remote security holes on everyone in order to do so. Yay progress?
This insecure and undocumented environment is enhanced further by the rock-solid and totally secure Windows environment. Sarcasm part 23 there in case you didn’t catch it. Windows is, and always has been un-securable because of Microsoft’s design choices. Microsoft will not secure Windows because it will cost them marketshare and money, something that far outweighs customer security in Redmond. Instead, Microsoft retroactively patches flaws, sometimes, and steadfastly refuses to fix the underlying flaws. This dance, accompanied by rather curious statistics from Microsoft funded studies, is about as transparent as it is futile.
Why is this important? Because you can’t run Small Business Advantage without Windows. Insecure hardware with un-securable software, both somehow deemed an advantage by Intel. It does make the mind reel, but far be it from Intel to do the right thing. If you recall, this is from the same brain trust that was terminally confused by the term false positive, and the less said about McAfee’s track record, the better.
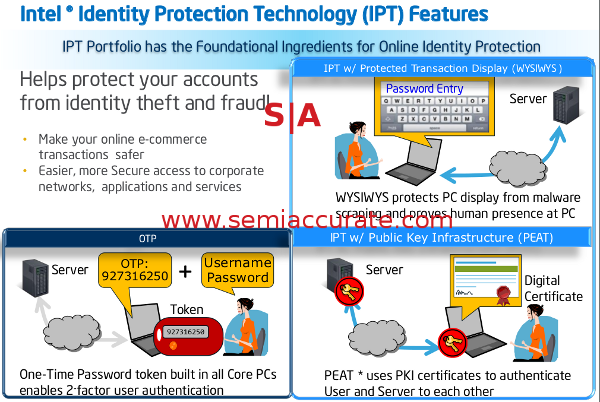
The first SBA item on the list is Intel IPT or Intel Identity Protection Technology. IPT is basically a one time key generator, normally a good idea. Unless it is built on insecure hardware, and requires Windows to run. We have been asking Intel for a technical briefing on some of these technologies for about a year and a half now. What did we get on IPT? A reassuring “It is secure, we say so, and you should trust us.” That, and this single slide.
Intel IPT, guaranteed secure because some PR person says so
If that doesn’t convince you to put your financial details on the internet, I don’t know what will, an animation perhaps? IPT is a good idea built on a scary and proven insecurable foundation, but it has cartoons to make you feel better. Ever seen a version of RSA’s secure keys that use embedded Windows or an Intel CPU? Think there is a reason for that state of affairs? RSA doesn’t use cartoons. Or Windows.
McAfee ePolicy Orchestrator Deep Command (MEODP) is another gem, described by Intel as, “an extension of McAfee’s leading endpoint security management offering that provides customers with remote security management access to a PC that is powered off or disabled. ” Great, now a hacked system is no longer safe from remote data theft once compromised. Think about this, if your machine is broken in to by bad guys that want to steal your data. Turning the damn thing off until you can get someone to deal with it is a really good idea, and the step that most people start with.
Now, thanks to vPro and MEODP, turning your machine off will not stop the flow of stolen data, you just won’t be able to tell that you are being cleaned out. Who at Intel green-lighted this silicon malignancy, and why do they still have a job? Oh yeah, McAfee, answered my own question. Luckily, that can’t happen, and it is guaranteed to be more secure than IPT. Why? MEODP has an animation to prove it, but Intel won’t tell you the basic technical details. (Warning: If you watch the linked video, you are at great risk of depression, suicide, and losing 17 or more IQ points. It is truly awful yet strangely devoid of any real information.)
Intel Secure Key is a real hardware Random Number Generator. This is a really good idea, and it works really well, something that we desperately need in 2012’s insecure environment. Actually, we needed it before 2003 when Via put their version in the x86 CPUs they make. Ironically, those CPUs cost less than what Intel charges you to not have that feature arbitrarily fused off in their CPUs. Progress? Yes. Ethical? That is your call.
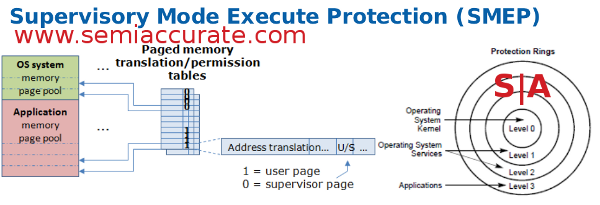
OS Guard, aka SMEP, we like SMEP better
OS Guard, excuse me, Intel OS Guard, is an interesting idea that prevents an OS from executing user code (Ring 3) when in supervisory modes (<Ring 3). This prevents some kinds of privilege escalation attacks, and in that is a good thing. That said, it currently needs Windows to actively support it to work, and that of course means running Windows. Think putting a very complex lock on a very strong jail cell door, but mandating the walls be made of rice paper because the sheriff’s brother has a rice paper business.
You would be vastly better off not using Windows and not having Intel OS Guard. That would of course negate the need to buy this extra security package that Intel thoughtfully removed earlier, so they will never support that eventuality. It is to their (Small Business) Advantage to keep you in the dark. If there is a problem, they will happily sell you more McAfee products to up corporate margins. This will make Windows secure, just like the last 17 things that were guaranteed to make Windows Secure. This time is different though, just like the last 17.
AMT 8.0 is short for Active Management Technology, and once again, Intel takes a potentially great idea, and screws it up. Why? It allows you to remotely wake up and do anything you want to a machine. If your machine is compromised, the bad guys can wake up your machine, take anything on it, and place arbitrary code on it too. You can’t stop them, bad guys can remotely lock you out, or just rob you blind without any way of an owner knowing what is going on, even if they have the machine in front of them. Data theft just got ugly.
But it gets worse. Intel touts this ‘feature’ as available on Ultrabooks. Think about that, Ultrabooks have wireless built in, and do not have removable HDs. Once your machine is compromised, if it is an Intel Ultrabook, there is literally no way to protect the data on it, reinstall, or even pull the plug on the data theft. Removable hard drives? Not on Ultrabooks. Pull the network cable? Wireless only, or worse yet 3G. Hard off switch for wireless? No room on the thin body, all software controlled. Pull the battery? Nope, can’t do that either. Basically, with Ultrabooks, once the bad guys are in, there is NO way to get them out without voiding a warranty and desoldering flash chips. Luckily, Microsoft security, aided by McAfee software, all built on an platform designed by people who don’t even understand the basics, has your back, protecting your valuables with walls of rice paper obscured by blizzards of press releases. (Editor’s note: Intel does not seem to print their press releases on rice paper.)
Luckily, Intel Keyboard, Video and Mouse (KVM) Remote Control is there to help. Not you, once your machine is rooted, the bad guys control this function too, so you are totally impotent to do anything, but if they are feeling charitable, they might let you watch. If they are not, they can lock you out, taunt you, or just run it silently as you play FarmTown VII in blissful ignorance.
Or they could just use Intel vPro Technology module for Microsoft Windows Powershell to script the entire attack. Then your data could be silently and unavoidably stolen, and your machines completely compromised with no hope of restoration, all with a small and totally automated script. How wonderful progress has become. If you have an Ultrabook with Small Business Advantage, then you are hosed so badly that there is no possible fix. Ultrabooks, disposable yet insecure, neither by user choice.
The short version of all this is that Intel has been proven to not understand security, stonewalls whitehat security researchers who bring up serious problems, and then takes literally years to patch holes with known exploits. All of this is baked in to all current Intel hardware, and there is no way to avoid it, and very likely no way to turn it off, you just make it invisible and unmanageable. Then Intel charges you more money for these ‘security and manageability’ features that they arbitrarily took away if you don’t pay their extortion money. On top of this, they require the single most insecure OS out there to work, and preclude compatibility for actually secure software by not documenting their ‘features’. This, in a nutshell, is Intel Small Business Advantage, something that you really should avoid. But you can’t.S|A