![]() At IDF, Rambus (NASDAQ:RMBS) was demonstrating the technology of their newest acquisition, Cryptography Research. Actually, they were not showing off what the tech could do, they were showing off what it could prevent, without spilling the secret sauce.
At IDF, Rambus (NASDAQ:RMBS) was demonstrating the technology of their newest acquisition, Cryptography Research. Actually, they were not showing off what the tech could do, they were showing off what it could prevent, without spilling the secret sauce.
Cryptography Research (CR) does something that sounds simple, they guard against side channel attacks on crypto hardware. Side channel attacks are things that don’t go after the numbers themselves, but look at the hardware for related information like power use, emitted EM, and other things that are not often guarded against. The idea is that you don’t read the output of the algorithm, you read the process itself.
At IDF, CR was showing off how to snoop several devices, mostly smartphones running crypto algorithms, in real time. While it was an ideal setting, their demos showed off how effective a side channel attack can be when in the hands of a layman. With someone who knows what they are doing behind the same tools, if you are not protected, your keys can be extracted more easily than a script kiddie looking at a Sony product.
CR was showing off power monitoring, magnetic field, and other EM emissions snooping. The smartphones were grinding away at several crypto programs, and they were put in front of various sensors to show what could be sniffed. The demo was simplified for, well, demo purposes, but the same techniques hold for real world sniffing. In the field, it is just a bit trickier to figure out what to look at, but you do the same things in roughly the same way.
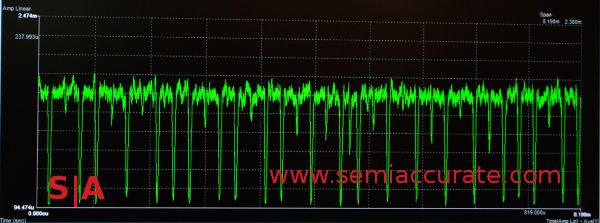
Power monitoring of a smart phone
The CR guys were monitoring the power use while one type of algorithm was used. A 0 in the key has one set of functions used to encode/decode the data, and a 1 in the key uses a much more complex series of calculations. That is the complex way of saying a 0 does a little work, a 1 does a lot of work. A 0 draws little power, a 1 draws a lot. Can you read the key, or at least part of the key?
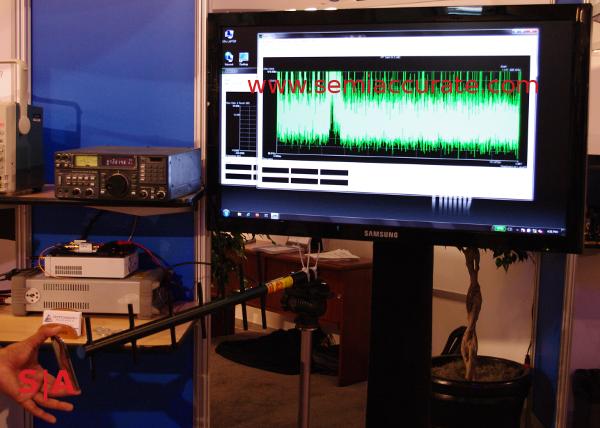
EM sniffing of keys works too
In this demo, you can’t actually see much because we held the device up to the antenna for the sake of the picture. You can see a little bit of the peaks, but the signal/noise ratio is so high that everything gets washed out. If you hold the phone back a ways, you can read the keys in a very similar way to the power sniffing above. Think about that for remote sniffing of keys, all you need is a directional antenna and a clear view of someone’s office……
Other types of attacks work the same way, you figure out what the algorithm is doing, and what the differences each bit or sub-section of the key produces. Then you just look for that, and if the devices is not protected, you simply read the keys off. In practice, it is a little harder than that, but if you know what you are doing, most cryptosystems can be shredded quite easily.
That brings us back to CR, and why Rambus bought them. CR provides countermeasures to this type of snooping, something you really need to do if you are in any way serious about security. Exactly how they protect you is kind of a secret sauce, so no answers here, but it does vary with each implementation. Some countermeasures are algorithmic, some are physical, and some are, well, secret.
In any case, as you can see above, if you don’t guard against this type of attack, your keys are vulnerable. Anyone trained in the art of side channel attacks can rip you to shreds in short order, and given how much easier it is than brute forcing keys, it is where I would start hacking. Luckily, there are some very smart people that can help keep your keys private too.S|A
Charlie Demerjian
Latest posts by Charlie Demerjian (see all)
- Qualcomm Is Cheating On Their Snapdragon X Elite/Pro Benchmarks - Apr 24, 2024
- What is Qualcomm’s Purwa/X Pro SoC? - Apr 19, 2024
- Intel Announces their NXE: 5000 High NA EUV Tool - Apr 18, 2024
- AMD outs MI300 plans… sort of - Apr 11, 2024
- Qualcomm is planning a lot of Nuvia/X-Elite announcements - Mar 25, 2024